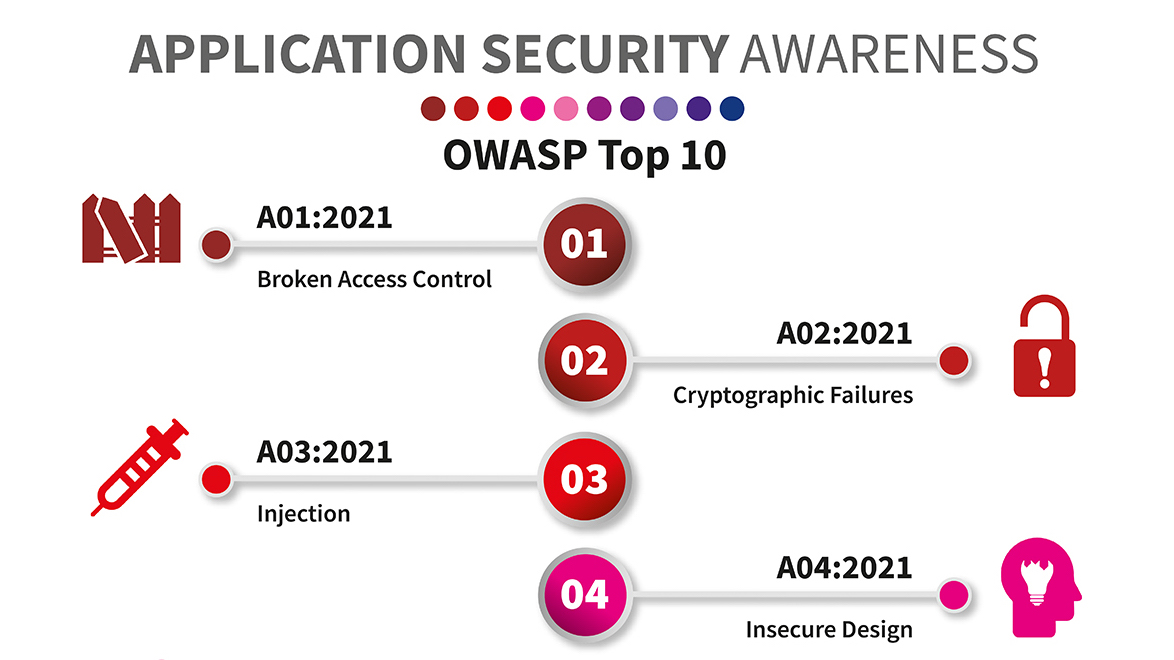
Kicking Off Security Maturity
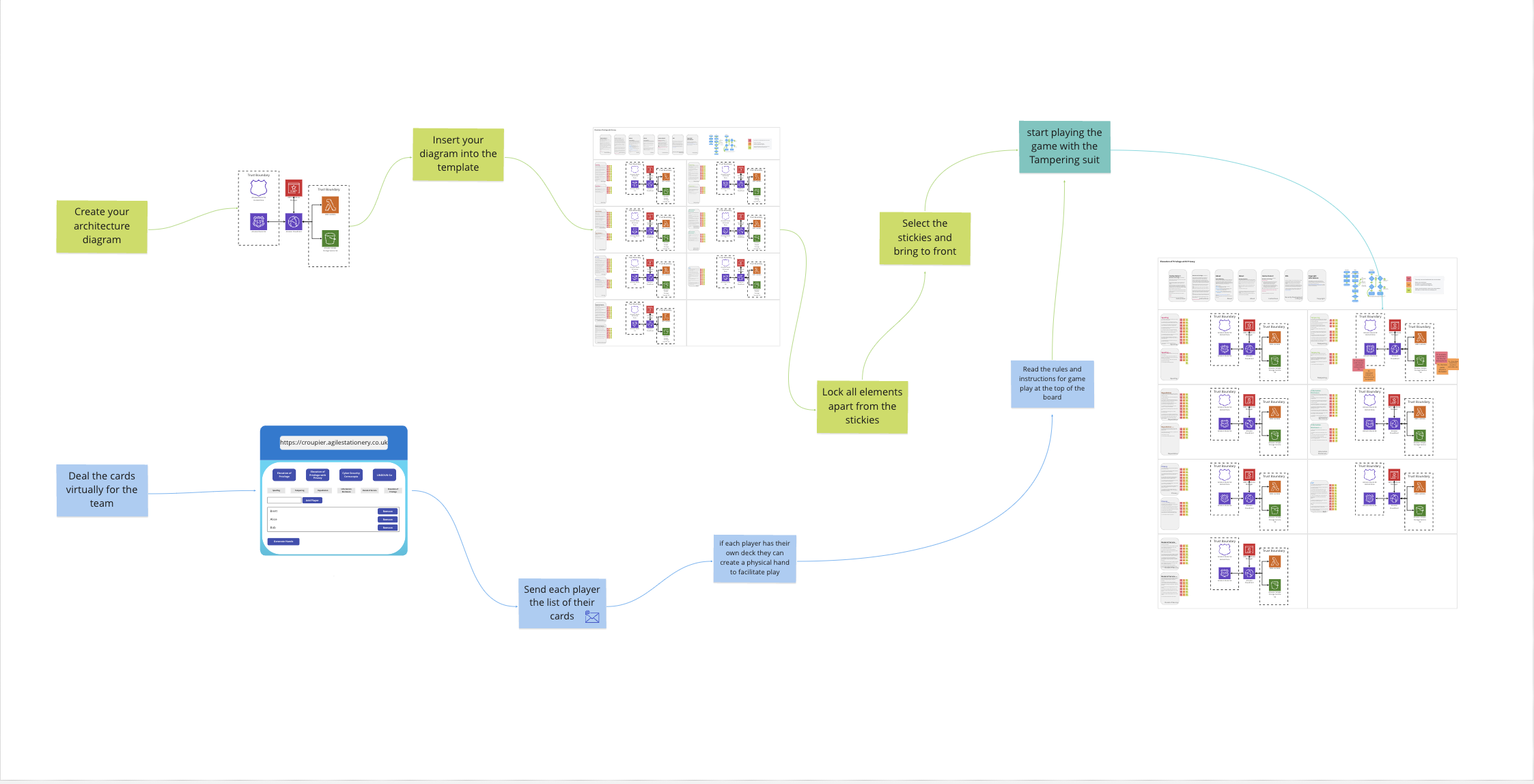
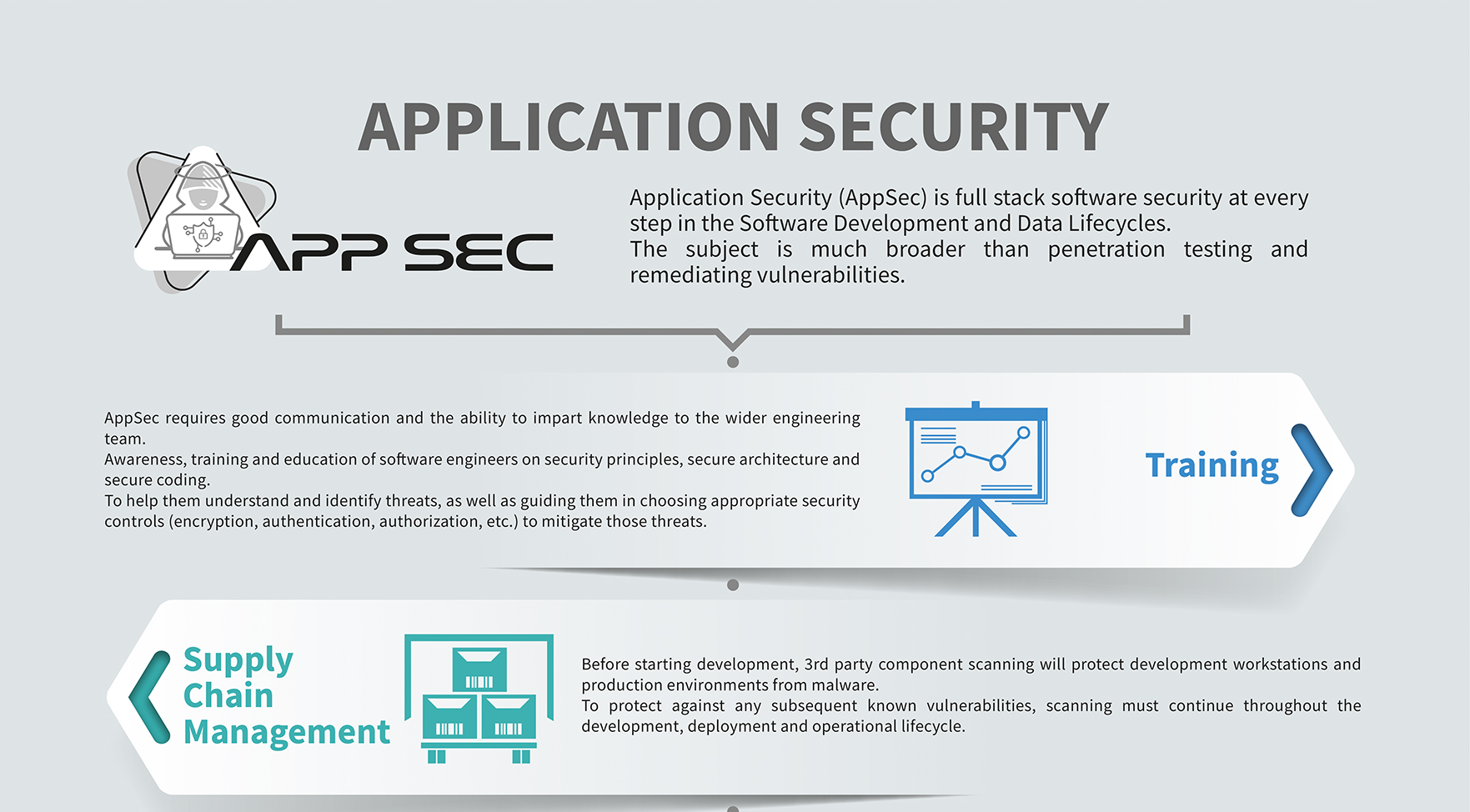
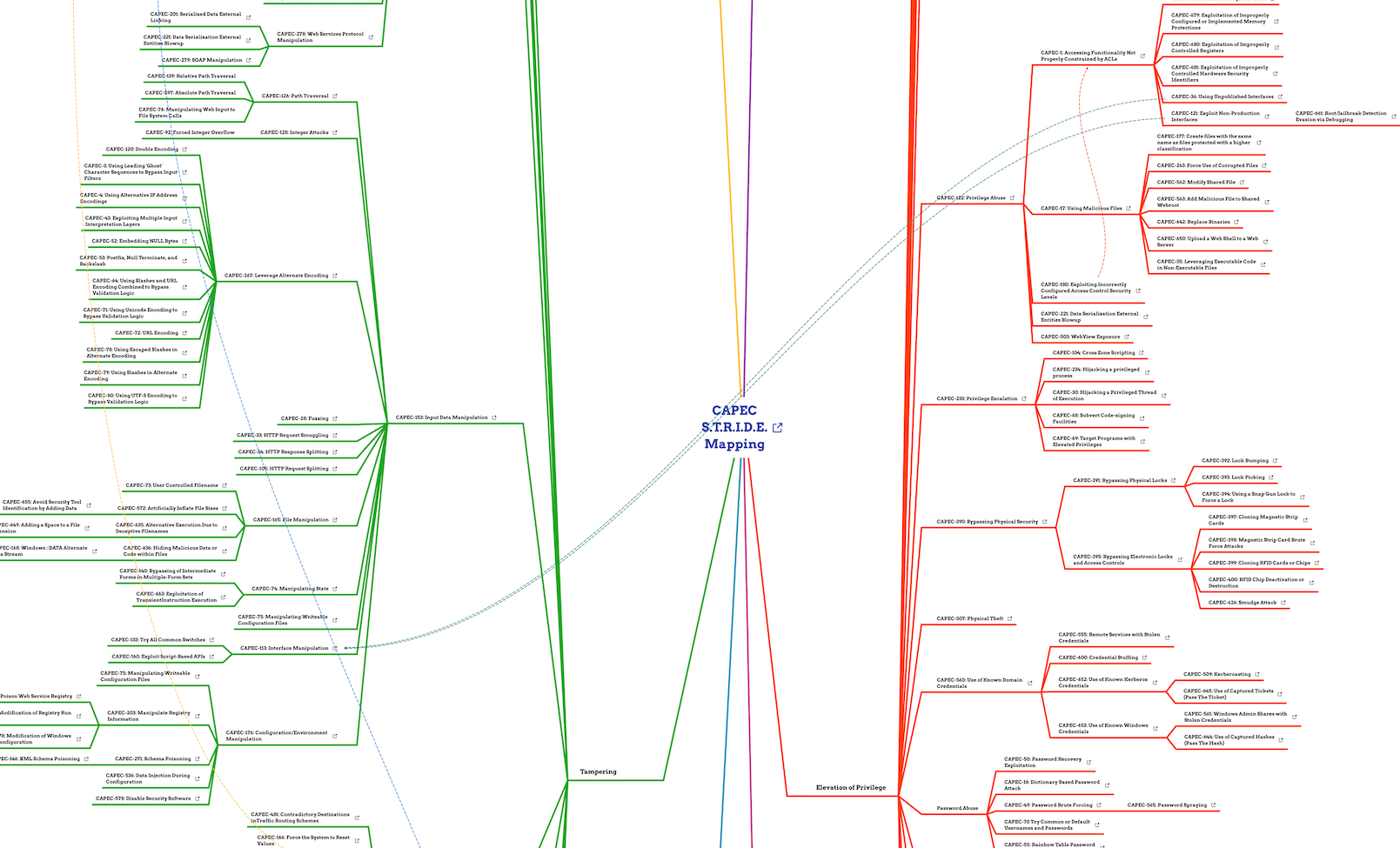
Building an AppSec Program: A Collaborative Approach Are you looking to kickstart an Application Security (AppSec) program? Do you want to assess your organization’s security maturity? Or perhaps you’re aiming to cultivate a stronger security culture? If any of these resonate with you, this method might be just what you…